In August 2009 I wrote about "Defensibility and Recoverability", in which I started developing the notion of using a legal basis for building a defensible position. I later expanded on this notion in the post "Creating Epic Fail Conditions: PCI and Best Practices", along with touching on it in a few other places. More recently, I used the idea of "legal defensibility" through the article "Architecting Adequacy: When Good Enough Really Is" in the March 2010 issue of The ISSA Journal (I'll post an ungated copy of the article when I get a chance). I also floated the idea at the ABA InfoSec Committee meeting during RSA, where I the response was very positive, including getting some air time on a couple panels in the LAW track at RSA.
So, that's a brief background, but what is it, really? What is "legal defensibility" and why do I think it amount to a new doctrine for the infosec community as a whole? More importantly, how can this new notion be used to successfully promote security initiatives, and why should you take it as a legitimate new argument and approach?
A Definition
Legal defensibility is defined as follows: An organization must proactively build a case that can withstand legal scrutiny, which demonstrates that it has done everything reasonable to protect itself and its assets in order to preserve and build long-term value. It should operate under the assumptions that it will experience a security incident, and that as a result of such an incident, it will be subject to legal proceedings (civil or criminal) that challenge whether or not it did what was necessary and reasonable in protecting itself. The principles inherent in networked system survivability, including defensibility and recoverability, should become the basis of the proactive approach to building such a case.
A Security Strategy
First and foremost, I view legal defensibility as a security strategy, rather than as a legal strategy. IANAL, and thus this is not legal advice. The main driving factor behind this approach is that the traditional arguments are tired and failed. We've been only marginally successful within infosec in compelling business and government to do what is necessary to protect its own interests, protect its intellectual property, and to do what is right for its shareholders, employees, and customers.
The best two examples I can give for why this is a plausible and useful security strategy are:
1) The case of Heartland: Heartland Payment Systems thought that they were compliance with PCI DSS. They thought that they were secure. However, as this interview with their CEO shows, they didn't look at security holistically, but rather took on blind faith that compliance with a single regulation (that only covered a portion of their environment) somehow made them "secure."2) Risk management confusion: Let's be honest for a minute and realize a couple things. First, outside insurance and financial services, very few organizations are doing true, formal risk management. Second, most "risk management" is based on a house a cards, failing to pin the risk ratings to anything meaningful to the assessed organization. As a result, there is generally a lot of confusion among executives and senior management about what information "risk" means at any given point in time. There's a failure to link the risk assessment findings to concrete business ideas.
The goal of legal defensibility is to provide a far less abstract approach to enterprise security that looks at the whole of the organization, starting from what is core to the business, and working on a couple key premises.
Fundamental Premises of Legal Defensibility
There are two fundamental premises that underpin the notion of legal defensibility:
* When, not if: The reality today is that all organizations should expect a security incident to occur. In fact, it's a reasonable expectation that every organization has already experienced, or is currently experiencing, a security incident of some type. These incidents may range from malware infections to targeted attacks to an actual data breach. Regardless, there can be no speculation about "if" an incident will occur, but rather the focus should be exclusively on "when" a breach will occur and then how your organization will respond to the breach.
* Protect what's valuable: As part of this doctrine, it is important to know what is important to the business (and we're really talking about material value here - if X is affected, then it will have Y impact on your business - that kind of idea). In my experience, businesses tend to intuitively know what is mostly important, but it seems rare - especially in the SMB space - that businesses are actually acting in their own self-interest these days (see my grip "A Sense of Self-Preservation" from February 2010). It is imperative that organizations know themselves very well, and that they then act in a self-preserving manner that looks at long-term value rather than obsessing over quarterly results.
There's also a bonus attribute that should be considered: Publicity of data breaches does not have long-term negative financial impact. Again taking the case of Heartland, they took an initial hit on their stock price (see this analysis from July 2009), but they're now back to trading around the same levels they were at pre-breach announcement (see Google finance: HPY). More importantly, they've developed a new product strategy that will undoubtedly add long-term value to their business.
The Key: Reasonability
Back to legal defensibility, then, as a concept, it's useful to understand the key to its success, and on what a lot of its viability will hinge: reasonability. In the court system, the concept of "the reasonable man" is often used to gauge whether actions were appropriate in a given context. This concept has ties back into the world of "common law" and if you're super-interested, I recommend taking a couple law classes just to see how crazy the legal system used to be. ;)
In this instance, there are two uses of reasonability that are core to the doctrine:
* Reasonable standard of care: A concept that I've heard lawyer bandy about, a "reasonable standard of care" essentially means that your organization has done what is demonstrably "reasonable" in protecting its assets. The key term here, though, is "reasonable" and whether or not your interpretation meets the interpretation of the general populace. The case I've heard referenced in a classroom environment is that of T.J. Hooper, where a shipping company didn't use technology that was "so extensive as to be a nearly universal practice or custom, but not required by statute," resulting in a major loss (to their client), resulting in their being found negligent. While this case may not be popular in modern case law, it nonetheless gives us a notion of how the courts can interpret "reasonable standard of care."
* Reasonably foreseeable: The other attribute here that makes the concept a bit challenging is that of what is reasonably foreseeable. We've already set the concession that it's not if, but when, an incident will occur. In building your defenses, and hedging with recoverability capabilities, what if you don't defend against the latest, greatest 0-day attack? Were you negligent? While this is certainly a concern, and a potential threat to this doctrine, the answer I think lies in the development of case law and the fair application of law. You should be prepared for 0-day vulnerabilities and exploits, and you should have a methodology in place for addressing them. However, it is not reasonable to expect that you will somehow have patched an 0-day before a patch is available, though you should be expected to have assessed the impact to your environment and taken reasonable compensating efforts to protect yourself in the interim.
The bottom line here is that you'll need to be prepared to make an argument to 12 angry men that demonstrates your organization did what was reasonable to protect itself and its assets. Failing to make such a compelling argument will inevitably result in a conclusion that your organization was not competent, may have been negligent, and who knows what else.
Not Just "Due Diligence"
My friend Alex recently wrote an article titled "Why I'm Skeptical of 'Due Diligence' Based Security" in which he talks about some potential failings in the traditional "due diligence" approach to security. As he rightly points out, this approach is really the same as the compliance mindset, which focuses not on doing what is right or adequate, but on doing the bare minimum to meet the technical requirements of regulations and agreements, but without doing what is necessary to protect the business itself.
Legal defensibility is about far more than due diligence. Due diligence and compliance, along with risk management, are certainly part of building a legally defensible position, but they are not the end - just part of the means to the end. Instead, legal defensibility is very broad, very flexible, and heavily emphasizing proactivity.
Inclusive, Holistic, Comprehensive
One of the comments I commonly make is that we need to throw out information risk management when we first start talking about legal defensibility. For too long we've tried to use a risk-based approach to securing the business, only to have it fail time and time again. The reasons for these failures are myriad, and to much to cover in-depth here. Suffice to say, there are a number of failings, ranging from the concept being too abstract (or, not tied concretely to business values) to the specific methodologies themselves being wrapped in controversy (true or fake), such as whether or not we have any reasonable way to estimate the probability that a certain bad thing will happen. Overall, I view risk management as being too myopic. It lacks the breadth of view and knowledge necessary to make quality decisions for the whole enterprise.
This is not to say that there is not a time, place, and purpose for risk management. Within a legal defensibility approach there is absolutely a place for risk management. In fact, in action you will find that you still very much need risk management - just not as the sole driving force. In fact, most areas of security management have a place in a legal defensibility case. How much do I believe this to be true? Enough so that I still believe that my TEAM Model v2 (picture below) still provides an excellent roadmap for implementing a legally defensible position. If you examine the picture (click to see it full-size), you will see that there is a place for knowing the business, a place for information risk management, a place for information security operations, and a place for quality and performance management (which includes audit, compliance, pentesting, code analysis, and various metrics and measurements).
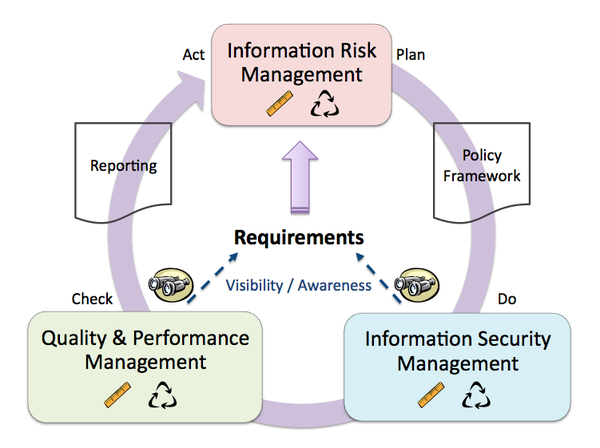
The point here is this: Legal defensibility doctrine promotes an inclusive, holistic approach to protecting the business. By it's vary nature, it cannot exclude anything that is reasonably part of a comprehensive strategy, barring measures that simply aren't cost-effective.
Promotes Proactivity
Perhaps the most important aspect of legal defensibility doctrine is that it promotes a proactive approach to protecting the business that allows the business to define itself in a manner that makes business sense. This approach requires de-emphasizing activities that are tied exclusively to regulatory compliance in favor of planning measures that benefit the business and help protect and grow long-term value. Simply put: if a given measure costs more than it benefits the business, then a legitimate argument can be made - proactively - that the measure will not be used simply because it does not add long-term value. As long as that analysis is reasonably complete, and that the decision is thoroughly documented for posterity, then it seems to follow that the position is defensible.
Codifiable
Part of the elegance in legal defensibility is that it is flexible in a way few other regulations currently are. And, unlike regulations like Sarbanes-Oxley (SOX) or Gram-Leach-Bliley (GLBA), though legal defensibility would not specify exact technical countermeasures, it does create the basis for legal arguments that go to the heart of competence and negligence in the managing of the business. If there is one thing American business culture could use right now, then it is a legal framework that sets the machinery in motion to start building case law around what can be reasonably expected of businesses in terms of protecting themselves and building long-term value.
Concluding Thoughts
Legal defensibility as a concept is still developing, but thus far all the feedback I've received has been extremely positive. It makes sense and is easily explained to people, regardless of their background. Part of the beauty in this approach is that the majority of people implicitly understand the goal: to make an argument that we did what we reasonable thought or knew to be right in protecting our assets.
At the same time, legal defensibility provides a strong tool to present to executives, boards, and senior management to say "listen, we are not doing what we need to be doing to protect ourselves, and it's going to lead to bad consequences." It also creates an excellent opportunity for security teams to partner with legal teams (who often hold more sway with executives and boards) to start making strong points that more needs to be done to protect the business from online threats. Add in the potential for codifying this as part of law, making negligent actions not only costly in civil court, but potentially criminal, and it seems likely that executives will start paying closer attention.
Hopefully you'll find this argument compelling. I look forward to your feedback. :)

Agree with the premise, especially given the legal bind that organizations can find themselves in under the standard of due care. One clarification - in the Hooper case the shipping company was held liable for losses that could have been prevented had the boats been using radios, even though the use of radios was *NOT* a widespread or universal practice at the time. The analog to modern security practice is, say you hold off on deploying a promising leading edge security technology until it becomes pervasive. If the plaintiffs in a civil suit against you successfully argue that use of the new technology would have prevented the loss, that's it, you're liable. This often exceeds what an organization might choose to do following the standard risk-based approach to security unless organizations inlude the potential loss to customers as part of their impact calculations. That's exactly what I like about your legal defensibility concept, because (as I understand it) it makes organizations consider what they should do in their own protection, instead of managing for compliance or some other misguided approach.
Thanks, Steve, you're absolutely correct on Hooper. I think this gets down to the question of what is or is not "reasonable" and "reasonably foreseeable." I think I misstated it a bit above (will look into that and change it as necessary). It seems in the case of Hooper that, while the use of radios was not prevalent on barges, if I recall the overall case correctly, the use of radios in general had become fairly widespread, including in other types of shipping operations. Arguing that "oh, it's not required or commonplace in my niche industry" isn't then a defense against adopting a technology that help mitigate a reasonably foreseeable threat.
Thanks for your additional comments, too. I think you've summarized things quite well.
-ben
I find it interesting how a business risk approach can be myopic and an approach to satisfy 12 angry men holistic? Legal defensibility is just another impact driver, of course you should add legal to your business justification. However I don't suggest leading with it. Sales manager, "first we had to do x because of compliance, now we have to do y because of lawyers." How about letting the business decide what's best after you educate them, including legal precedent? Determining acceptable risk (Risk Management) isn't that hard if you align with the business goals and make them participate in the decisions.
Courts will define a new floor just as compliance has. Aiming for it may not be best for your business.
Given the lawsuits cropping up post breach, I think my comment last year was a bit myopic… The first big precedent where a defendant is compliant but not legally defensible will be a whopper!
It's good to see that you're coming around on this topic, Jared. :) My belief is that legal defensibility provides a sound, rational basis that could be codified easily while allowing us to move away from the particularly limited compliance mindset. The bar will continue to move forward over time, which will increase pressure on the business to not only properly assess its position on matters, but to also revisit those positions over time (i.e. what's adequate today may become inadequate tomorrow). Perhaps even more importantly - and inline with evidence-based risk management - is the notion that these decisions should all be thoroughly documented, dramatically shifting the burden onto the plaintiff.
Nice article. I find it interesting how a business risk approach can be myopic and an approach to satisfy 12 angry men holistic? Legal defensibility is just another impact driver, of course you should add legal to your business justification. Thanks for sharing this information..........
Thank you
Bizworldusa